Intro
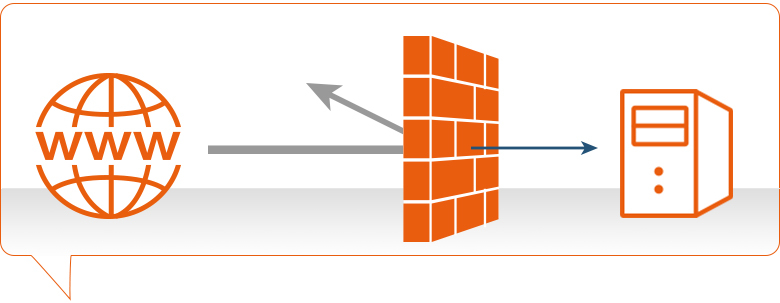
Without exception, if you are an experienced security analyst, then you know the importance of firewall logs and the invaluable network traffic related data that they provide. Many of the key strategies of information security revolve around the network traffic of an organization and the rules that govern it. No matter the type of firewall, whether it is a hardware appliance or a software/OS level...